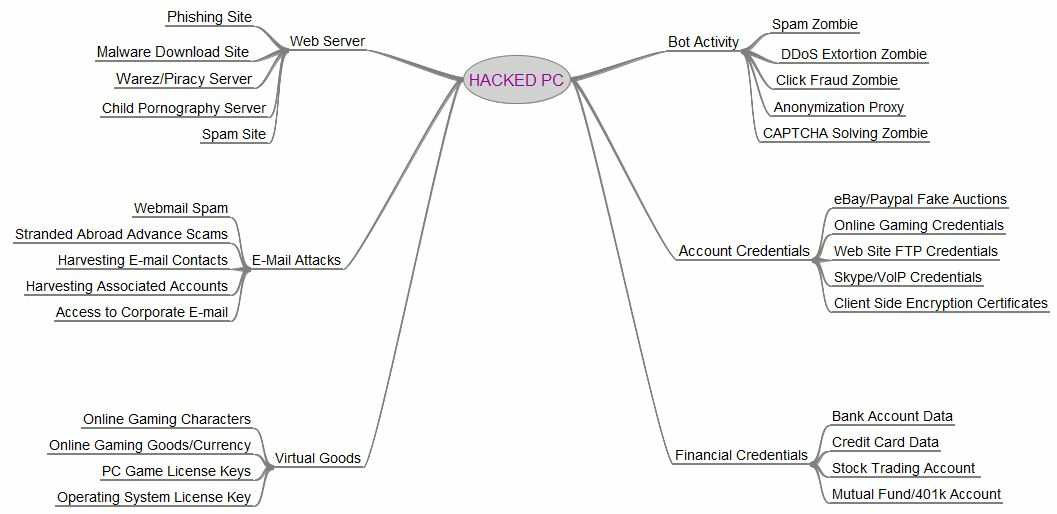
For some reasons, the configuration of mwserv in say, dionaea is perhaps among the mysterious question that I could find when I want to know the info.
Few years ago, I registered my honeypot as a "freelance" at
Mwcollect Alliance. Here, the maintainer (from Giraffe Honeynet - Germany based honeynet chapter) needs you to contribute back. In my case, I turned on the mwserv config in my honeypot.
In dionaea.conf (or any honeypot that you have, let say, mwcollectd), you need to uncomment mwserv in the ihandlers section:
ihandlers = {
handlers = ["ftpdownload", "tftpdownload", "emuprofile", "cmdshell", "store", "uniquedownload",
"logsql",
"virustotal",
"mwserv",
// "submit_http",
// "logxmpp",
"nfq",
// "p0f",
// "surfids",
// "fail2ban"
]
}
Next, once your registration approved in mwcollect alliance, you will be able to create your honeypot sensors.
mwserv = { // ask your mwserv backend provider for needed values
url = "https://mwserv.mwcollect.org/" // the url to send the submission requests to
maintainer = "" // username of the maintainer of this sensor
guid = "" // guid of this sensor, as generated serverside; typically 8 chars
secret = ""
// shared secret used for authentication aka password; typically 48 chars
}
Perhaps, people hard to find the url for mwserv, so as for last few years, it always been "https://mwserv.mwcollect.org/" .. this couldn't be find anywhere as far as I know, unless you hang out in #nepenthes channel at irc.freenode.net
You can filter the verbose output once your start you dionaea sensor:
dionaea -l all,-debug -L 'mwserv'
Output:
[01032012 08:24:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat
[01032012 08:24:45] mwserv dionaea/mwserv.py:166: mwserv heartbeatresult: b'OK: 120'
[01032012 08:26:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat
[01032012 08:26:47] mwserv dionaea/mwserv.py:166: mwserv heartbeatresult: b'OK: 120'
[01032012 08:28:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat
[01032012 08:28:47] mwserv dionaea/mwserv.py:166: mwserv heartbeatresult: b'OK: 120'
[01032012 08:30:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat
[01032012 08:30:48] mwserv dionaea/mwserv.py:166: mwserv heartbeatresult: b'OK: 120'
[01032012 08:32:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat
[01032012 08:32:46] mwserv dionaea/mwserv.py:166: mwserv heartbeatresult: b'OK: 120'
[01032012 08:34:41] mwserv dionaea/mwserv.py:77: mwserv _heartbeat